Unifying threat context with VirusTotal connectors
sophistication and
frequency, the pursuit of a unified threat contextualization platform is no
longer a mere convenience but an absolute necessity. When faced with an
unfamiliar file, hash, domain, IP address, or URL, having a singular view of
threat intelligence not only expedites investigations but also helps
eliminate detection blind spots.
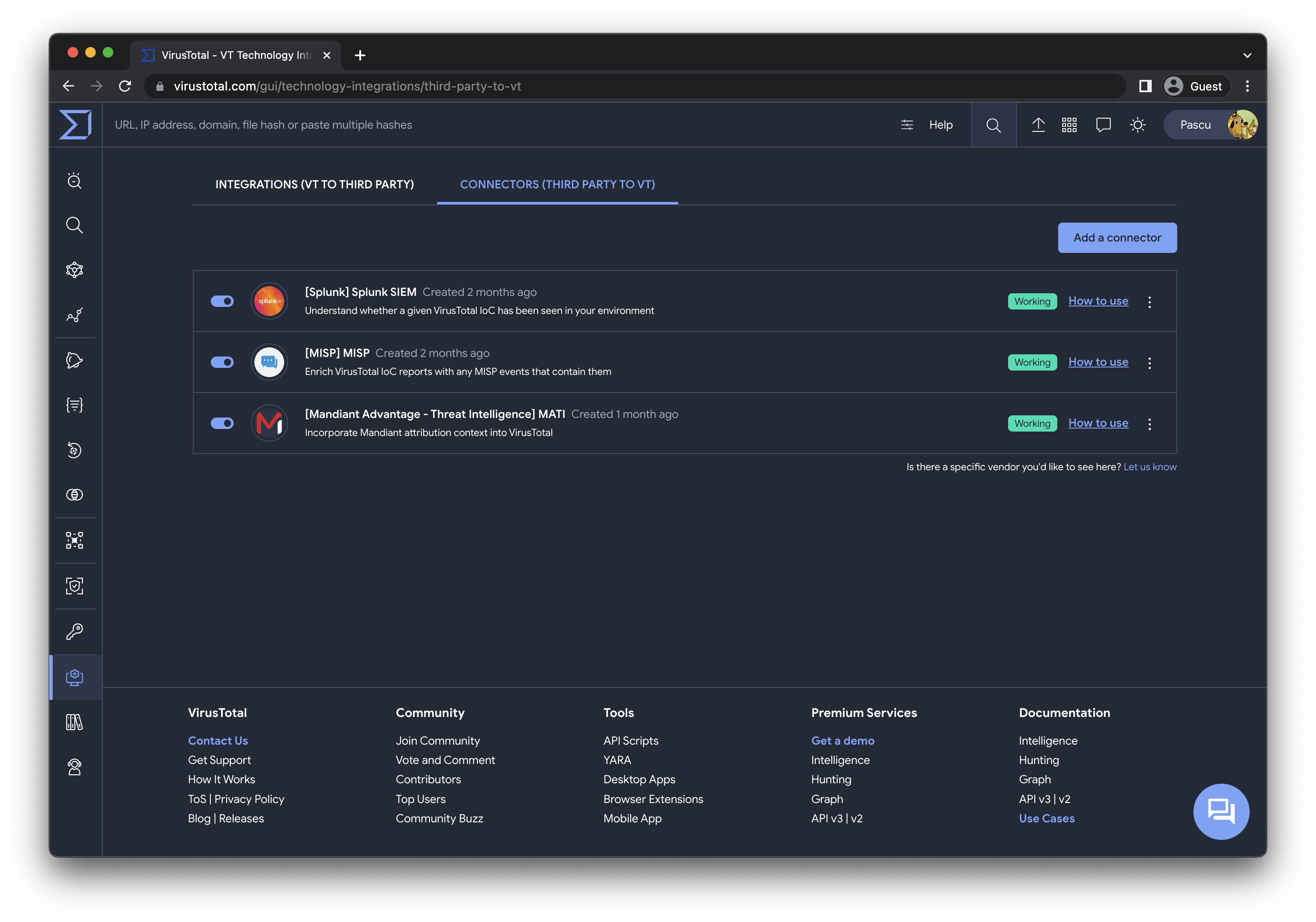
this unified
threat contextualization with VirusTotal Connectors. That’s right. All your
Threat Intel intelligence from third parties will seamlessly be merged with
VirusTotal’s context!
Complementary threat context
While this post doesn’t delve into specific third-party connectors,
we’re excited to announce that Mandiant is among our first supported
connectors. More details about this will be covered in an upcoming
blog post.
In addition to Mandiant, we are introducing two other connectors,
each offering distinct context for different use cases, provided by
leading security providers:
-
Mandiant Intelligence
–
This connector allows you to incorporate Mandiant’s malware
toolkit, campaign insights, and threat actor attributions into
VirusTotal. Learn more. -
MISP
–
Enhance VirusTotal indicator of compromise reports with
information from MISP events, including descriptions, tags, and
other pertinent data generated by your Cyber Threat Intelligence
(CTI) team and trusted circles. Learn more. -
Splunk
–
Gain immediate insight into whether a specific VirusTotal IoC
has been detected in your environment, either presently or in
the past. Learn more.
Configuration made easy
the configuration settings in the “Technology Integrations” section, under the “Connectors”
tab. This is also accessible via the left navbar menu in
VirusTotal Enterprise or the top navbar in its landing, under
the Intelligence entry.

is configure API
authentication for the corresponding intelligence provider
(bring your own license), and VirusTotal will automatically
retrieve any context that such a third-party provider may
have on any indicator you query in VirusTotal. This
contextual information will then be seamlessly integrated
into VirusTotal IoC reports, becoming the first section in
the Detection tab and it will be available only for you and
your group. At this time the connector’s information will
not be available via API. For additional guidance, please
refer to our documentation.
Community development
Our journey doesn’t stop here. We’re
already in the process of supporting more
data providers. At VirusTotal, we firmly
believe in the power of community
collaboration. We’re contemplating the
release of a framework that empowers our
community and third-party providers to
create and contribute their own connectors,
embodying our commitment to crowdsourced
security.
connect one of your threat intelligence
sources or an industry player seeking
support for your solution, please do not hesitate to contact
us.
Read more: Unifying threat context with VirusTotal connectors