Multisandbox project welcomes ReaQta-Hive
We are pleased to announce the addition of ReaQta-Hive to the multisandbox project, after the integrations of Tencent Habo, VirusTotal Droidy, Cyber adAPT ApkRecon, and Dr. Web vxCube. The unique new feature that this integration brings is XSL documents in addition to PE files, PDF, MS Office documents and scriptlets.
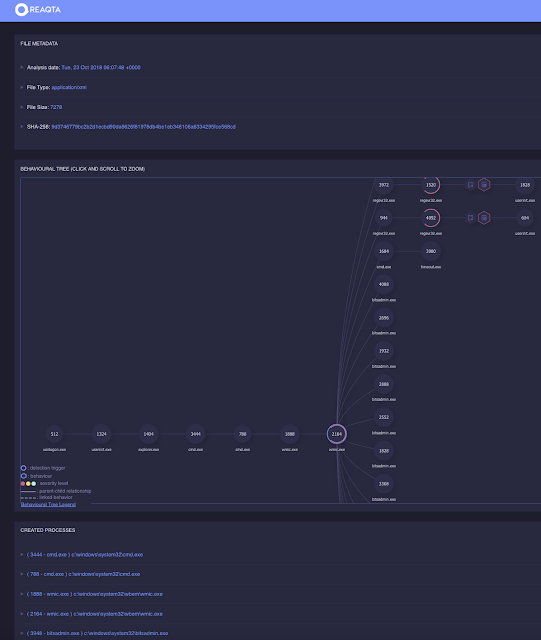
ReaQta-Hive is an Endpoint Threat Response and Hunting platform that uses A.I. to detect new types of attacks. A live hypervisor, called the NanoOS, collects detailed security information at the lowest possible level of an endpoint, which Hive uses to perform dynamic behavioral analysis. This analysis is automatic and constructs a comprehensive storyline of an attack. The end result is an intuitive report of all the actions carried out by an attacker, including a summary of the meta-behaviors that highlight key components of the attack. ReaQta-Hive is a vector-agnostic platform, so it can analyze the behavior of any type of attack, whether it is file-less, script-based, exploit driven, or a plain executable file. We are happy to use our software and expertise to contribute actively to the VirusTotal community, and to help analysts worldwide be more effective and efficient.
To view the ReaQta report when viewing a file analysis, click on the Behaviour tab, select ReaQta-Hive, then the detailed report.
XSL document / #squiblytwo
https://www.virustotal.com/#/file/9d3746779bc2b2d1ecbd90da8626f81978db4be1eb346106a6334295fce568cd/behavior
In the relationships tab you can see a link to VT Graph where you we can see some relationships to other domains and URLs VirusTotal has seen before.
Malicious document using LOLBins
https://www.virustotal.com/#/file/1f4f22f1814712880b2bbdc5c6418aeaf08c598be0990c5fad55136c9e769951/behavior
Windows PE file, detecting behaviors like key-logging/screenshots
MS Word document, executing powershell with emotet infection
Behavior report:
https://www.virustotal.com/#/file/6dcd70d4e0d78a7aa12d8e4ae85d503fc7d642a9f5e950f43803c3471753ab6e/behavior
Viewing in VirusTotal Graph, we can expose the network infrastructure involved.
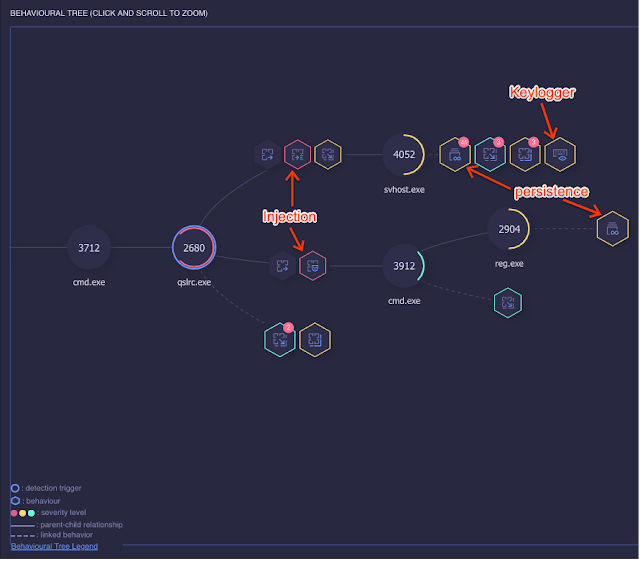
Malicious Document dynamic impersonation, then drops keylogger
Take a look at the ReaQta detailed behaviour report linked from the VT page at:
https://www.virustotal.com/#/file/24d94671e38f8f2f4c2f158e011a24c4641994b14962b3c4343308efdfb8fa71/behavior
 |
| Within the process tree, you’ll notice the process-hollowing (dynamic process impersonation) icon: |
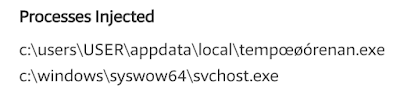
This also shows up in the “INJECTED PROCESSES” section of the report:
In the VT Graph we can see the relationship to the DDNS host and keylogger that is dropped.
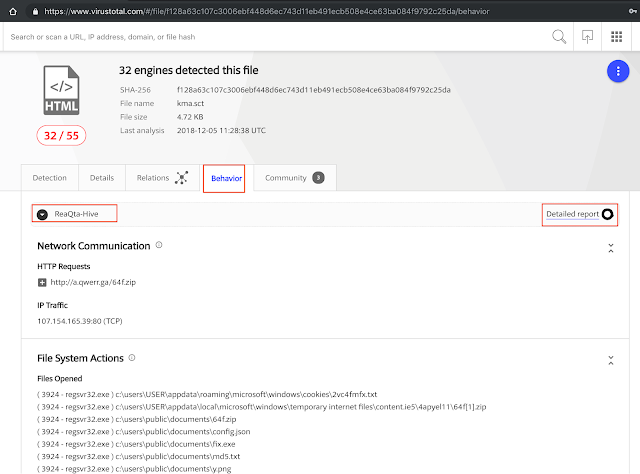
Windows Scriptlet (SCT) file
In the file https://www.virustotal.com/#/file/f128a63c107c3006ebf448d6ec743d11eb491ecb508e4ce63ba084f9792c25da/details we see a scriptlet file dropping a miner.
Have a look yourself by checking out the behaviour tab:
Read more: Multisandbox project welcomes ReaQta-Hive