Rootkit Cafe
Have you ever wondered about the ads you might have seen being shown on the desktop or in the browser during web browsing sessions at Internet cafes? One of our Analysts, Wayne, certainly did.
He recently analyzed a sample (SHA1: c8c643df81df5f60d5cd8cf46cb3902c5f630e96) that gave him an interesting answer. The sample was a rootkit named in its code as LanEx, though we detect it as Rootkit:W32/Sfuzuan.A:

Wayne traced the sample back to an advertising company in China called 58wangwei that runs an affiliate program for cafe operators looking to maximize the profits from a constant stream of eyeballs staring at their PCs. Their solution? Display ads to the cafe users.
The marketing spiel on the advertising site mentions that ” a single PC in the Internet Cafe operates 20 hours per day in average, excluding the PC idle time”. While we don’t have any statistics that would back that claim, very informal personal observation would seem to support it.
Anyway, interested cafe operators are directed to a webpage where they can download a software package (with the installer for the rootkit). The page includes a control panel to configure various functions in the rootkit, for example the default page it sets the web browser to. The various options available are all search engines almost exclusively targeted to mainland China. Each option has specified dollar amounts – for example, 26 yuan for 1000 unique visitors to one engine.
The operator then manually installs the package (which will then download the rootkit) on their computers and presto! They should be coining money right? Not quite – it’s not all smooth sailing for the operators. At least one support forum (Chinese language only) has operators asking for more details about the package and griping about it causing BSOD on their machines:
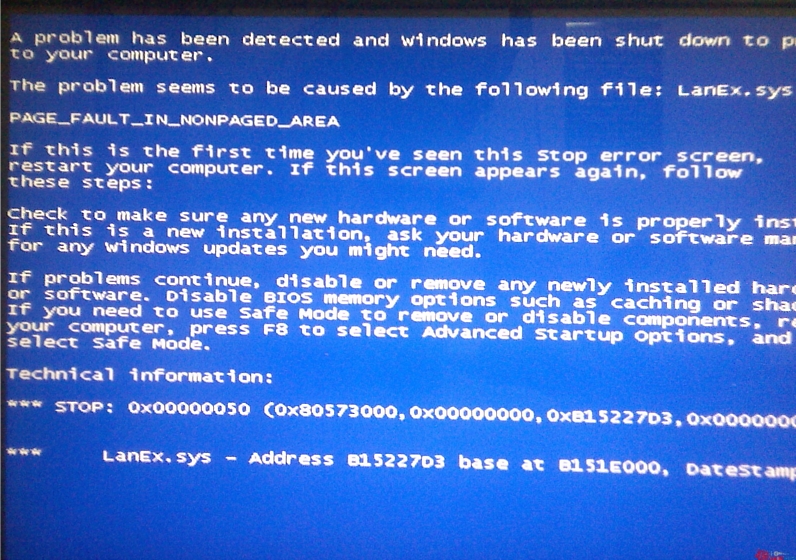
(source: bbs.icafe8.com)
Most of the operators aren’t actually aware what the rootkit is doing on their machines. The program is mainly aimed at displaying advertisements:
• Hide the processes belong to the advertising modules through SSDT hook
• Prevents the advertising modules processes from being terminated through SSDT hook
• Prevents access to certain webpages (based on the URL’s IP address and port number) through NDIS hook
The control panel on the webpage where operators download the installer for the rootkit also include the option to select which processes they want to hide in addition to the ad module-related processes, which are hidden by default.
Technically, the most interesting part of the rootkit is that it uses an NDIS hook to filter all the HTTP request and response messages sent over the network. If a prohibited HTTP request is encountered, the packet is modified and a crafted HTML page is returned by the rootkit.
The HTML page is either a hidden iframe or HTTP 302 redirection that redirects the user’s browser to a specified website:
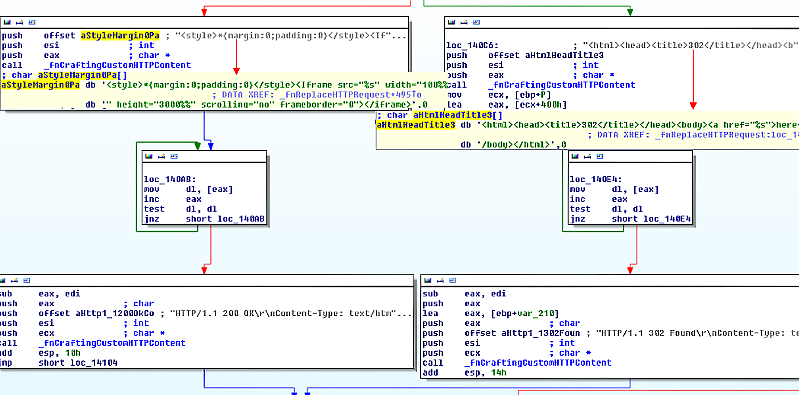
For users, the result of having the rootkit on a machine they’re using is inescapable exposure to advertisements. They may also be redirected to unsolicited websites.
Though the rootkit is mainly directed at displaying ads, it isn’t adware – it is still fully capable of performing far more malicious actions on the system. And it looks like even the Internet cafe operators don’t always know quite what they’ve installed on their machines.
On 13/09/13 At 08:13 AM