Ransomware spam e-mails targeting users in Italy and Spain
In the past few days, we received some cases from our customers in Italy and Spain, regarding malicious spam e-mails that pointed to Cryptowall or Cryptolocker ransomware.
The spam e-mails pretended to come from a courier/postal service, regarding a parcel that was waiting to be collected. The e-mails offer a link to track that parcel online:
When we did the initial investigation of the e-mails from our standard test system, the link redirected to Google:
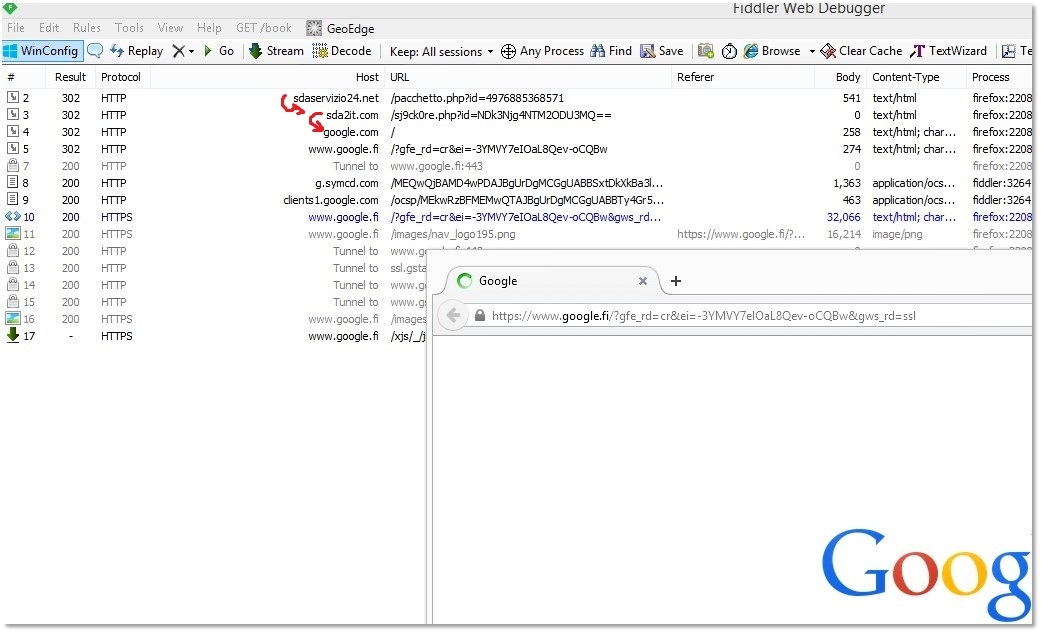
So, no malicious behavior? Well, we noted that the first two URLs were PHP. Since PHP code is executed on the server side, not locally on the client, it is possible that the servers were ‘deciding’ whether to redirect the user to Google or to serve malicious content, based on some preset conditions.
Since this particular spam e-mail is written in Italian – perhaps only a customer based in Italy would be able to see the malicious payload? Fortunately, we have Freedome, so we can travel to Italy for a little while to experiment.
So we turned on Freedome, set the location to Milan and clicked the link in the e-mail again:
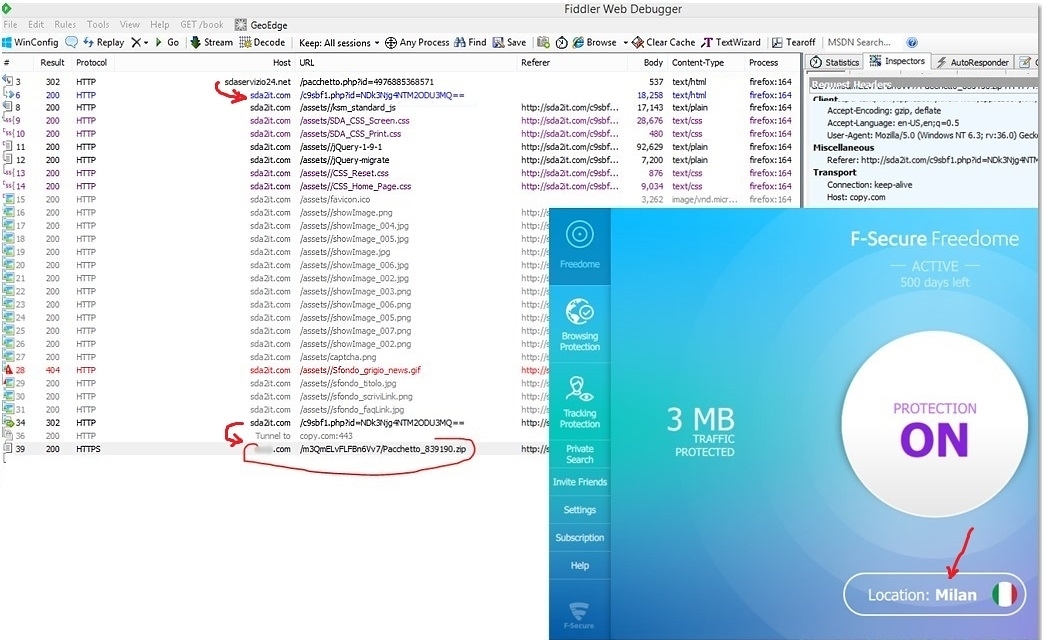
Now we see the bad stuff. If the user is (or appears to be) located in Italy, the server will redirect them to a malicious file hosted on a cloud storage server.
The e-mail spam sent to Spanish users is similar, though in those cases, a CAPTCHA challenge is included to make the site seem more authentic. If the link in the e-mail is clicked by a user located outside Spain, again we end up in Google:
If the site is visited instead from an Spanish IP, we get to the CAPTCHA screen:
And then to the malware itself:
This spam campaign doesn’t use any exploits (so far), just old-fashioned social engineering; infection only occurs if the user manually downloads and executes the files offered on the malicious URLs. For our customers, the URLs are blocked and the files are detected.
(malware SHA1s: 483be8273333c83d904bfa30165ef396fde99bf2, 295042c167b278733b10b8f7ba1cb939bff3cb38)
On 19/05/15 At 03:17 AM
Read more: Ransomware spam e-mails targeting users in Italy and Spain