Tinba – Yet Another Anti-Sandbox Trickster
Malware authors certainly do not take a breather when it comes to inventing new tricks for detecting sandbox, a very useful system to automatically analyze millions of samples nowadays. Recently, Seculert unveiled an unprecedented sandbox detection method that was employed by the Dyre/Dyreza malware. We have seen similar anti-sandbox tricks used by the notorious Tinba banking trojan and would like to discuss our findings, which could be helpful in improving sandbox technology. Joe Security has also seen the same evasion technique seen in Tinba in one of their samples.
User interaction combo detection
In the latest Tinba sample, we found it adopted an evasion technique where it checks for mouse movement using the GetCursorPos API. Additionally, its author has also introduced a new way to detect sandbox using the GetForeGroundWindow API, which enables the malware to check on the active window which the user is currently working on.
An automated sandbox system typically stays in the same window, and this could be a desktop from the point where the malware was executed. The malware tries to take advantage of this situation by checking for the values returned by two consecutive calls of the GetForeGroundWindow API. There is a couple of seconds interval between the two calls to simulate a real user interaction with the window. If the sample was executed on a sandbox environment, the values returned by both GetForeGroundWindow API calls will always be the same. This indicates that the current active window remains the same since the sample was executed. In this case, the code will keep looping and will only execute the main routine until the active window has been changed and the mouse cursor has been moved.
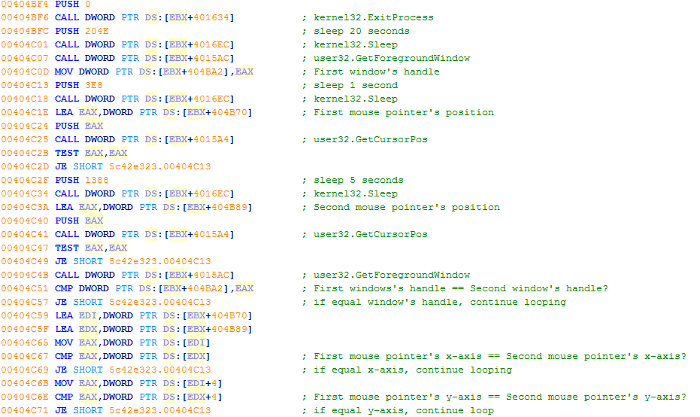
I hope I’m a real machine
Before executing its main routine after the user interaction detection, Tinba will employ another trivial evasion technique that is somewhat similar to the detection of the number of CPU cores done by Dyre/Dyreza. In Tinba’s case, it looks for the number of cylinder available on the running machine. Basically, this is similar to checking for the disk capacity. Perhaps due to the ease of implementation, it only checks for the number of cylinder on the disk using the ioctl code IOCTL_DISK_GET_DRIVE_GEOMETRY_EX instead of the finding out the physical size of the disk. In this particular case, it determines whether the disk has at least 5000 (0x1388) cylinder, which is around (11GB), otherwise the sample will quit. Just like detecting the number of CPU cores, checking for the disk capacity could be an effective evasion technique because regular computer machines nowadays should have more cores and disk space.
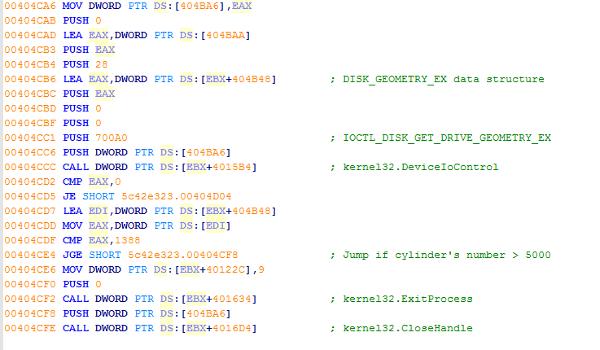
Tinba demonstrates that it can detect a sandbox simply by testing user interaction on a window and by checking for the disk capacity on a machine. When hardening their sandbox technology, other sandbox providers should keep in mind that malware authors are relentless in pursuing new ways to evade detection and thus, should make adjustment accordingly to keep up with them.
Tinba sample used in the analysis – 5c42e3234b8baaf228d3ada5e4ab7e2a5db36b03
On 06/05/15 At 06:46 AM
Read more: Tinba – Yet Another Anti-Sandbox Trickster